IAM Solution
SWAWE IAM
Identity and Access Management
One of the main challenges of ITGC controls concerns the perfect mastery of the user management process.
Implementing an Identity & Access Management (IAM) solution not only becomes an important ally for compliance, but also represents a significant gain in terms of efficiency, time and costs.
IAM solution, operating principle:
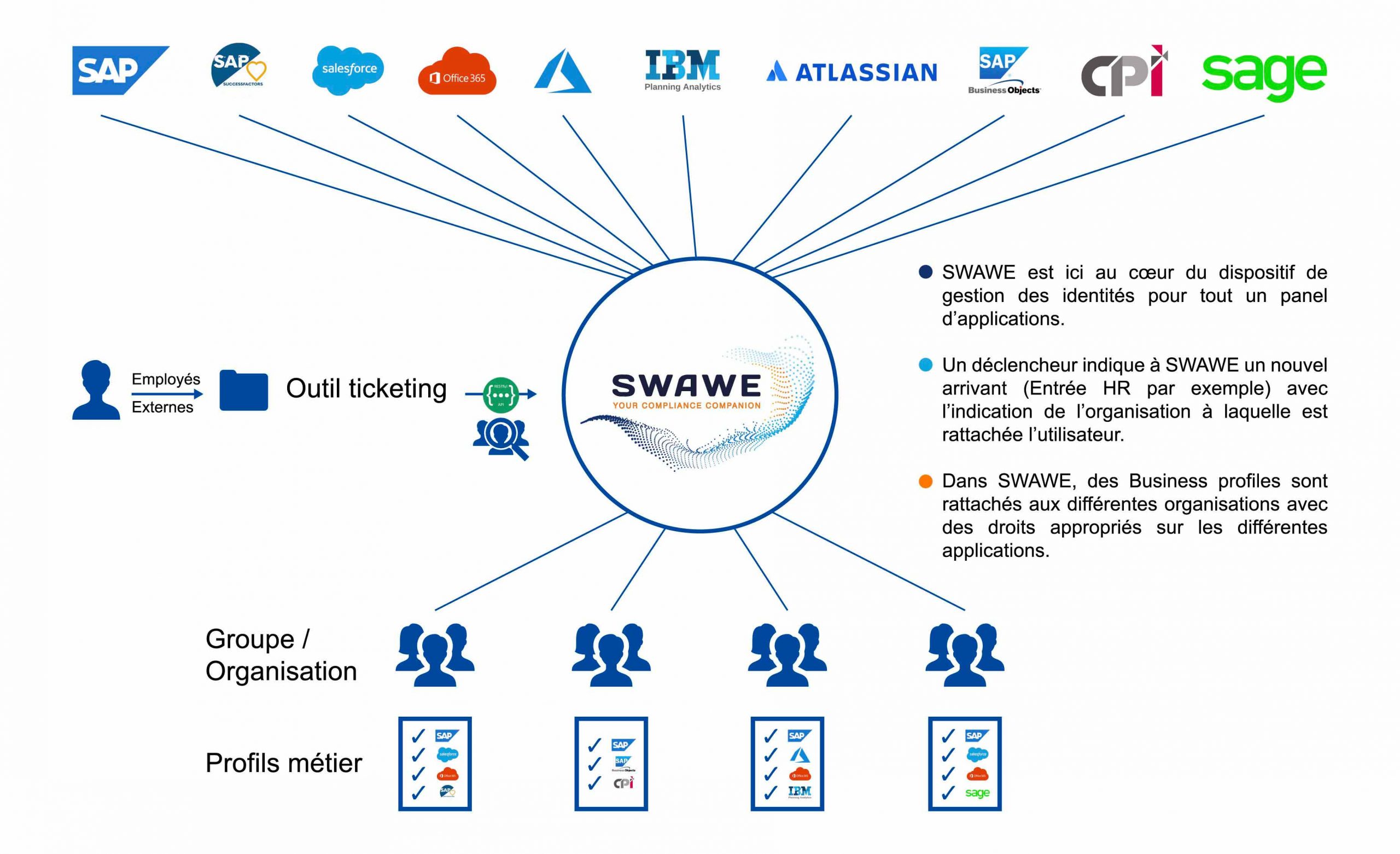
The SWAWE IAM identity management module allows you to define an organization, Business Profiles (groupings of rights in the various connected remote systems) and automate the management of the user lifecycle.
It is in an automated, centralized and secure way that identities are managed in the various connected systems.
Our customers particularly appreciate the integration with their existing tools, as illustrated here:
Main benefits of an IAM solution
Accurate mapping of identities and access
Integrating an IAM solution is a way to improve and automate identity management so that all of the following elements are considered: identity and authorization governance, organization and processes, data sensitivity classification, segregation of duties (SOD), and application rights provisioning.
Quality and compliance of your data
SWAWE allows you to store and log all actions related to identity management and application rights assignment. The automation of the various processes parameterized in the IAM guarantees the quality and compliance of the information contained therein.
Simplified role assignment management
Having set up in SWAWE a repository of IT applications (with authorizations by business profiles), automated validation circuits (by workflows), parameters filled in by default according to the organization of the beneficiary of the rights implicitly simplifies the management of the assignment of rights.
Main features of the SWAWE IAM solution:
Identity Management Automation
Managing and controlling the user lifecycle is often difficult because most of the time processes are done "manually" without a tool that centralizes and automates processes related to application security. SWAWE enables this automation by ensuring compliance with the approval, traceability and segregation of duties process.
Preventive risk analysis
Critical risk analysis or SOD can be done at any time in SWAWE. In the project or maintenance phase, it is sometimes useful to be able to simulate changes in rights assignments to know the impacts on risks, without actually assigning the rights. It is a preventive risk analysis.
Customizable approval workflow
To comply with best practices, it is necessary to set up a validation process when creating or updating the user file. Workflows can be defined at different levels: during the validation of the request by a manager (in connection with the attachment of the beneficiary to an organization), during the validation by a process owner risks the SoD analyses, during a validation by an additional interlocutor to complete / validate the initial request ...
Integration with your existing tools
SWAWE can be used independently, but it can also be integrated into the mapping of existing company applications. This prevents the company from multiplying its applications and thus maintaining a tool that centralizes its identities and associated application rights. Interactions from a technical point of view between the company application and SWAWE take place via APIs.
Custom reports and dashboards
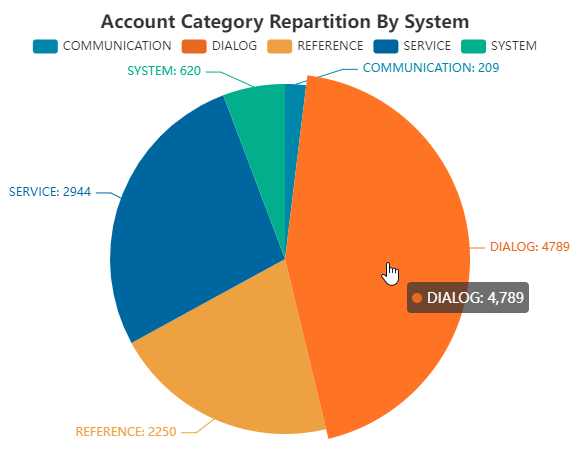
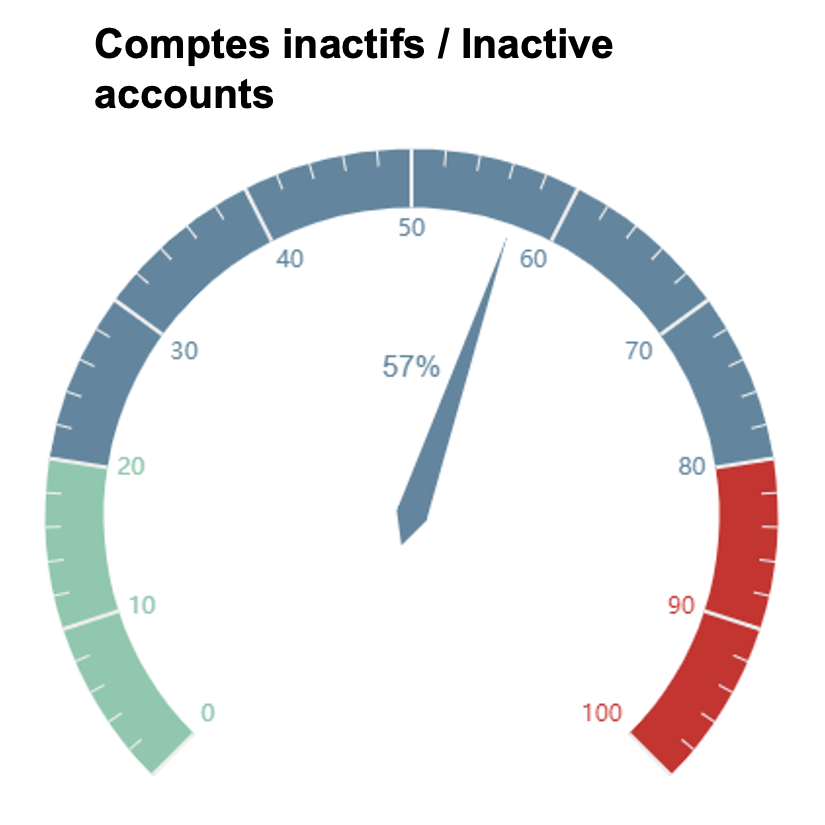
SWAWE has by default a set of tables that allow you to create dashboards or reports according to the needs of the company. In the context of IAM, we can, for example, set up reports on active/inactive accounts, on the types of users, on new risks that appeared during the last creations, or create detailed lists with the use of transactions or with the details of risks or with the name of the associated business rights...
Materialization of evidence for auditors
SWAWE allows you to store and log all actions related to identity management and application rights assignment. From the request to create a user to the provisioning of it in the system, all information is traced and historized, and therefore auditable.